By Neil Blazevic, TC116 Student
(Also published on Medium)
At DefendersTech we have spent years training human rights defenders and journalists in the East and Horn of Africa on security tools including email encryption tools such as GPG. These tools were created so that parties to a communication could take their privacy into their own hands and not rely on companies like ISPs, email providers, and social media companies to safeguard their privacy for them. Most GPG tools remain cumbersome to use but once you master them you will better understand the parts and relationships of an encryption infrastructure: public keys, private keys, message encryption, message signing, and key verification.
As it turns out, these are the same concepts needed to understand Bitcoin and other cryptocurrencies: instead of sending and receiving messages, you send and receive money/value; instead of using public keys to identify yourself, you use it to identify your wallet (and private keys to spend from it); instead of using email infrastructure, you use blockchain infrastructure — a global network of parties reaching consensus on transactions and the balance of everybody’s wallet.
Cryptocurrency as Financial Human Rights?
Cryptocurrencies are arguable an evolution of human rights ideas in the domains of finances: financial self-determination, self-expression, and privacy. Bitcoin, the first working cryptocurrency, was created by the anonymous ‘Satoshi Nakamoto’, continues to be developed by volunteer programmers across the globe working by consensus and collaboration, and is operated by self-interested private citizens and companies. It is not backed by any nation state or central bank, and it bypasses centuries of banking regulation, international financial controls, and financial surveillance. It is smart, fast, cheap, programmable money. It breaks the stranglehold nation states, banks, and industry power players like Visa and Mastercard have on money.
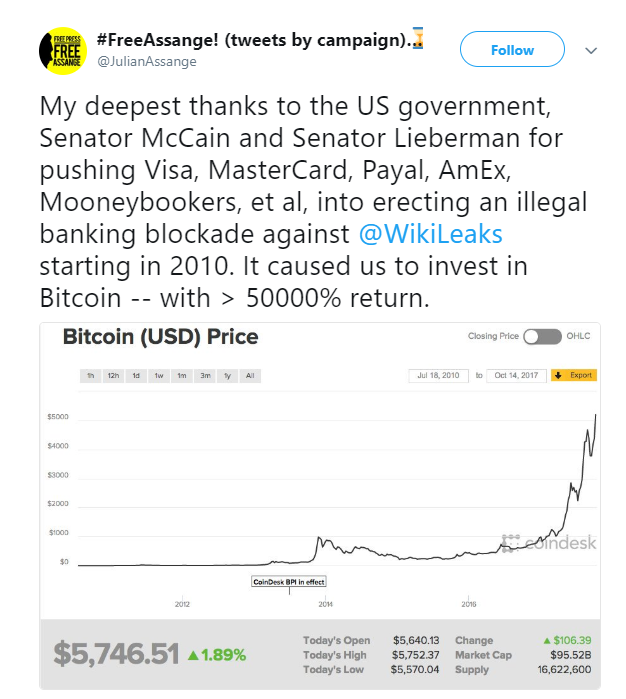
When payment processors and banking institutions fell in line after being instructed by US authorities to cut off donation channels to Wikileaks, the controversial government leaks platform asked the public to use Bitcoin instead. In late 2017, when Bitcoin was in the midst of its stratospheric 2017 bull run, Wikileaks gloated on Twitter that those US instructions had turned modest donations into a significant war chest. The idea that donations to political and social causes are protected acts of free speech is one that has legal backing in many jurisdictions, and Bitcoin enabled the exercise of that right.
New cryptocurrencies, so-called ‘privacy coins’, have launched since Bitcoin which address these gaps in privacy. These coins include Monero, Zcash, Dash, and ZenCash.
Much more than money: What use for human rights defenders?
In addition to cryptocurrencies, which serve as a store of value, their underlying blockchain technology can also power a dizzying array of applications which benefit from having a decentralised, immutable, consensus-based ledger. These applications include file storage, communications, publishing, asset ownership, legal contracts, official interactions, voting, autonomous digital democracies, digital (and self-sovereign) identity, and much more.
Privacy features of cryptocurrencies can apply to decentralised blockchain applications as well. How will privacy features get baked in to blockchain applications? How will blockchain applications effect the human rights equation as they emerge both as decentralised anarchic entities as well as in use by existing centralised authorities as governments and industry contemplate adoption? What new human rights fights will need to be fought? What new tools will come into the hands of human rights defenders?
At the recently-concluded World Blockchain Forum in Dubai, I had the pleasure to talk with Robert Viglione, Co-founder and President of ZenCash. ZenCash is building exactly some of these applications on top of their privacy-focused blockchain network include private messaging, file storage, online publishing, and making access to the network censorship-resistant.
We talked ideal users, usage for human rights defenders, new tools, usability, and online democracy. Read on for the full interview, edited lightly for readability.

An Interview with Robert Viglione, Founder of ZenCash
Q: Why did you decide to create a privacy coin?
RV: The whole point of it was to create a censorship-resistant network so people could have privacy on their transactions, privacy on messaging, privacy on publishing. It was really designed to open the world up and tear down borders.
Q: Who do you expect to use ZenCash?
RV: The first group is people who care about privacy. People in the Bitcoin world who realised it isn’t very private — That was our first audience. Now we are trying to build out our audience and mainstream it. The core audience is people who need privacy around the world.
Q: Do you see any use case for activists, dissidents, human rights defenders?
RV: Of course that’s who we think about as the user. That’s where the censorship resistant aspect comes from, and why we have it. I think it’s a perfect tool for them.
Q: What are the new applications you’re building on ZenCash and how can they be used by human rights defenders?
RV: ZenChat is messaging which lets users communicate with each other without fear of repression or surveillance even for people who are in parts of the world which deny them access to parts of the internet. We’re developing a domain fronting application called ZenHide which hides your access to the network. It looks like you’re using a Google server or an Amazon server and it’s designed to get you into the network so you can use all of our tools.
Then ZenPub is for secure publishing — if you’re a journalist in a repressed part of the world or a whistleblower and want to publish something without fear you can do it with ZenPub.
Q: Security tools are often difficult to use, how usable are the Zen tools?
RV: The first generation was not very usable. The second generation will be very usable. Right now we have what we call “operation radical usability” which is a huge product push to redesign our products and make them super simple for new users. I’ll be honest, the first generation products were really designed for more technical users, just to have something out there already that they can use.
Q: What else in the blockchain space are you excited about?
RV: I’m looking at liquid democracies concepts like what we’re doing with our voting systems, because we want to empower people and this can be used for communities where you can have proof of fair elections, or figure out how you can do resource allocation together. I really like those applications because I think it’s an interesting governance domain — not just publishing and accessing networks, but once you’re a networked community, do you have a voice in that community?
I think our voting system within ZenCash is the most exciting — not just because I’m biased but because it actually comes from game theory research. We’re solving two big issues with voting systems and DAOs [decentralised autonomous organisations]. One is that you don’t want the voting system itself to influence the outcome, so we have secret balloting. We use our privacy technology where at the end of voting the votes are revealed, rather than having them revealed along the way which could tilt the vote. The other issue is voter apathy — we want to overcome it by actually paying the voters. So we use a bit of economics there. It’s cool because as a member of the community you can actually earn an income by being a good citizen.
Q: Thanks so much Rob!
RV: My pleasure Neil.
Coda
I do hope to contribute to a conversation about usage of blockchain for human rights promotion and by human rights defenders. How will cryptocurrency, privacy coins, blockchain applications especially with privacy features built-in be of use in their hands? Please share your thoughts in the comments, Twitter, new posts, etc!
Learn about Blockchain: What is blockchain? The most disruptive tech in decades (ComputerWorld) | Still don’t understand the blockchain? This explainer will help (World Economic Forum)
Learn about Bitcoin: www.bitcoin.org
Learn about Zencash: www.zencash.com
If you would like to donate cryptocurrency to the work of DefendDefenders, we would love to accept it. We are currently working on a policy to enable this within the formal structures of the organisation. Shoot us an email at crypto@defenddefenders.org to be notified when we begin accepting cryptocurrency donations.
Neil Blazevic is the DefendersTech program manager at DefendDefenders, an organisation committed to protecting and supporting human rights Defenders across East and Horn of Africa, and CTO at BlockchainAG, a Uganda-based blockchain service company. Tweets from @neilblazevic.
TechChange’s “Blockchain for International Development” course is back September 10! Sign up here!